In a recent press release, we announced that Spherical | Analytics (S|A) had been chosen to participate in a use case consortium sponsored by the National Institute of Standards and Technology’s (NIST’s) National Cybersecurity Center of Excellence (NCCoE). This opportunity places us in a position to put our technology at the forefront of collaborating on cybersecurity solutions for critical infrastructure.
The Cooperative Research and Development Agreement (CRADA) focuses on securing information exchanges among IIoT (Industrial Internet of Things) controllers from distributed energy resources (DERs) in their operating environments. These operating environments can be some of the most challenging from a physical and digital architecture standpoint and are persistently confronted with myriad cyber and climate risk challenges.
Figure 1: Distributed Energy Resources visualization by RTO Insider[1]
DERs represent a core pathway to revolutionize the energy grid through the physical distribution and logical decentralization of security and optimization of these smaller resources. Some sample DERs growth statistics and metrics[2]:
US distributed solar installations are projected to grow from 2.0 to 3.8 million between 2018 and 2022 (GTM Research)[3]
Behind the meter battery storage is forecasted to grow from 200 MW to 1400 MW between 2018 and 2022 (GTM Research)[4]
Electric vehicle sales will increase from 1% of new car sales to over 50% by 2035 (Energy Innovation)[5]
S|A plans to contribute the Immutably™ platform, Proofworks™ service layer, Scrivener™ distributed transaction ledger, ProvenPaths™ contextual state engine, and EdgeShare™ layer to support the mission of accelerating the adoption of best of breed cybersecurity technologies and to provide real-world standards-based cybersecurity capabilities.
The project will address the following areas of interest:
· the information exchanges between and among DER systems and distribution facilities/entities and the cybersecurity considerations involved in these interactions
the processes and cybersecurity technologies needed for trusted device identification and communication with other devices
the ability to provide malware prevention, detection, and mitigation in operating environments where information exchanges are occurring
the mechanisms that can be used for protecting both system and data transmission components
data-driven cybersecurity analytics to help owners and operators securely perform necessary tasks
The outputs of our collaboration in the CRADA will document the reference design for securing IIoT in commercial- and/or utility-scale DER environments and will include a reference implementation solution that uses existing, commercially available cybersecurity products.
ENABLING DISTRIBUTED SECURITY IN CYBERSPACE
In the landmark white paper, “Enabling Distributed Security in Cyberspace: Building a Healthy and Resilient Ecosystem with Automated Collective Action,” published on March 23, 2011, the National Protection and Programs Directorate (NPPD), US Department of Homeland Security (DHS) presents three building blocks as foundational for a healthy cyber ecosystem: automation, interoperability, and authentication.[6] These three fundamental principles enable Automated Collective Action (ACAs) through continuous monitoring, much like that of the human immune system.
Figure 2: The human immune system as a model for distributed, autonomous security systems proposed by the NPPD[7]
Context Labs’ technology achieves each of these three fundamental items through different service layers that all interoperate themselves as part of the Immutably™ trust platform, and with other key enabling technologies in various cybersecurity and digital trust approaches.
Automation or, “strategies that incorporate decisions made and actions taken in response to cyber situations,” requires a technological solution designed with those processes or services in mind. With the ProvenPaths™ configurable context state engine (CSE), structured and unstructured data can be processed through defined paths or workflows to ensure proper security, veracity, and authenticity of any data or asset. The automation of that data or workflow becomes built into the engine itself and fortified by the rest of the Immutably™ stack and cybersecurity solution.
Interoperability, the second building block, is achieved when it “enables common operational pictures and shared situational awareness to emerge and disseminate rapidly.” Complex cybersecurity solutions often consist of numerous, disparate technology providers and their own proprietary software. Oftentimes, a one size fits all solution ends up creating greater friction as multiple contributors to the same cybersecurity solution cannot properly integrate or interoperate. Scrivener™, while capable of serving as the transaction ledger itself, can also help reduce this friction. The Scrivener™ distributed transaction ledger tackles this challenge with its own interoperability with many other popular ledger approaches.
Authentication, the third and final building block defined in the paper, “should enable trusted online decisions […] and provides appropriate assurance that the participants are authentic or genuine, and it should do so in a way that enhances individual privacy.” With the deep trust and provenance provided by the Proofworks™ cryptographic proofing service, the ImmutablyTM stack offers deep, persistent authentication with multi-party participation, that allows users to generate and apply multi-point cryptographic proofs of critical digital assets across their lifecycles. The customizability, provenance, and security of the Proofworks™ solution enables that collaborative ecosystem of trust.
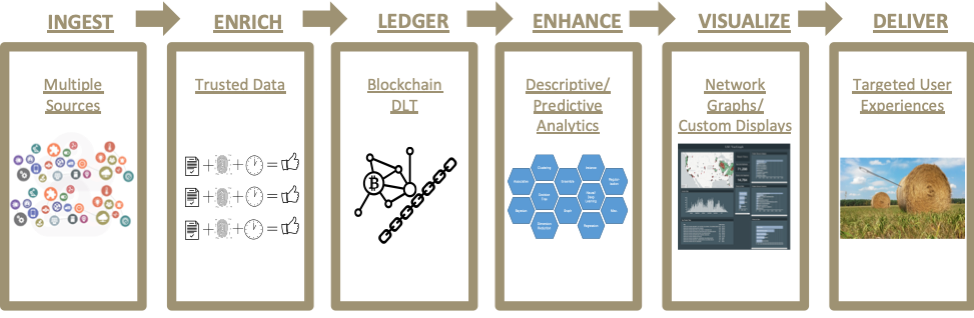
Figure 3: An example workflow through the Immutably™ stack
Armed with these capabilities among others from our partners in this program that support these three principles, a complete cybersecurity system for a DER can execute multiple ACAs on a potential bad actor. Real-time alerting and monitoring allows for early identification of suspect messages for quarantining, reverting, honey-potting, or any other pre-determined routine to ensure security for assets at the edge. Additionally, an immutable record of any potential attack or unauthorized access allows for a forensic review of any attack to help prevent future incursion.
Most exciting for us will be our contribution to the publicly available NIST Cybersecurity Practice Guides also known as the Special Publication 1800 series of documents. This series of publications result from other research opportunities such as this one and are designed to provide guidelines and standards for the implementation of cybersecurity solutions. By setting industry best practices, NIST hopes to enable others to repeat and reuse these standard tools and methods for more faster, more cost-effective widespread adoption.
[1] https://rtoinsider.com/distributed-energy-resources-der-44978/
[2] https://www.utilitydive.com/news/how-leading-utilities-are-planning-for-distributed-energy-resources/516260/
[3] https://www.woodmac.com/reports/power-markets-u-s-solar-outlook-initial-reactions-to-section-201-decision-58115523#gs.kOvUkvM
[4] https://www.woodmac.com/research/products/power-and-renewables/us-energy-storage-monitor/#gs.Yu_rqyM
[5] https://energyinnovation.org/wp-content/uploads/2017/09/2017-09-13-Future-of-EVs-Research-Note_FINAL.pdf
[6] https://www.dhs.gov/xlibrary/assets/nppd-cyber-ecosystem-white-paper-03-23-2011.pdf
[7] https://www.dhs.gov/xlibrary/assets/nppd-cyber-ecosystem-white-paper-03-23-2011.pdf


![Figure 1: Distributed Energy Resources visualization by RTO Insider[1]](https://images.squarespace-cdn.com/content/v1/5a525e56f9a61ed1f686e875/1581359107319-93TG7IWBPTRV3ZER3HU9/Distributed+Energy+Resources+visualization)
![Figure 2: The human immune system as a model for distributed, autonomous security systems proposed by the NPPD[7]](https://images.squarespace-cdn.com/content/v1/5a525e56f9a61ed1f686e875/1581359192730-F7YS8ORCXHDUL2XDTYSE/human+immune+system+as+a+model+for+distributed%2C+autonomous+security+systems)